- Home
- News
- “High-secret mobile phone” was successfully hacked by hackers? One technique “can cure all diseases”!
“High-secret mobile phone” was successfully hacked by hackers? One technique “can cure all diseases”!
Following the five-in-one information warfare of “sea, land, air, space, and electricity”, cyberspace with the Internet as the main battlefield has developed into the sixth largest strategic space. From “increasing Internet penetration” to “intensifying Internet use”, information security protection has become the main theme of Internet development.
As the most important direct access terminal of the mobile Internet, the mobile phone was initially limited to making calls and sending and receiving text messages, and gradually developed into a smart device integrating search, social networking, gaming, payment, location services, and mobile office applications. It can be described as “a personal computer that you can carry with you”, and the challenge of information security has gradually spread from the traditional PC to the mobile phone, and it is becoming more and more intense.
Although major mobile phone manufacturers are committed to introducing new products, the information security of smartphones is still a spark. The over-open mobile phone system has various insecure factors that cause the information of the majority of mobile phone users to leak, which is tantamount to “streaking in the wild.”
“Hacker Attack”
The current popular view is that the Apple ios system has advantages over the Android system in terms of data confidentiality and information security. The Apple App store is stricter and more closed when reviewing software, and can better protect user privacy.
However, not long ago, CCTV Finance exposed a major loophole in Apple mobile phones and other devices: hackers can get all the information on Apple devices without touching the mobile phone!
The vulnerability was discovered by a senior information security researcher at Google. It took him six months to break through the security line of an iPhone in the next room. In just 2 minutes, he successfully hacked through the air and controlled the phone. During the whole process, the target phone worked normally without warnings, pop-up windows, or any signs that might alert the user of being hacked.
The key to this vulnerability is an “AWDL Network Protocol” on Apple. Through this loophole, hackers do not need to use disguised e-mail or SMS URLs to induce users to click, they only need to be on the same WiFi to fully access the target iPhone or other Apple devices.
After the intrusion is successful, the hacker can not only view all the personal information in the mobile phone, but also conduct real-time monitoring. Even if the user manually closes the AWDL protocol, the hacker can still re-enable the protocol and control the user’s device.
Although Apple has fixed this vulnerability in the new system, and although it took a long time for researchers to break through the security line of Apple’s system, we cannot deny that the majority of users’ mobile phones are still remotely controlled by hackers, personal information has been stolen, and personal behavior has been compromised. The danger of surveillance.
“Fire in the backyard”
Coincidentally, not long ago, Gionee mobile phones, which claimed to be a pioneer in the field of mobile phone information security, rushed to the black list of “information security”.
Gionee mobile phones had previously focused on “security functions”, which improved the stability and security of mobile phones through multi-dimensional encryption. However, in November 2020, it was exposed that Gionee’s subsidiary had implanted a “Living Trojan virus” into more than 26.51 million mobile phones without the knowledge of its customers, thereby making illegal profits.
From December 2018 to October 2019, Beijing Baice Company and Shenzhen Zhipu Company jointly implemented “pulling activities” (successful executions) a total of 2.88 billion times.
Since April 2019, the number of “pulling” devices covered every month has exceeded 21.75 million, of which 26,519,921 Gionee mobile phones were involved in October 2019.
From December 2018 to October 2019, Shenzhen Zhipu Co., Ltd. estimates that it can earn RMB 27.85 million from Beijing Baice Company’s “pulling” business, and the “pulling” expenses settled by both parties are RMB 8.425 million.
Gionee’s subsidiary Zhipu Technology and its partner Beijing Baice, the core members of its team are basically from Microsoft, Baidu, 360, Cheetah, Tencent, Ali and other leading cybersecurity industry companies, and they have considerable expertise in big data and information security. experience of.
By updating the version of the “Story Lock Screen” software, they implanted Trojan horse programs into the user’s Gionee mobile phone, automatically updated the version without the user’s knowledge, and received instructions to increase the activity of APP users (also known as “Live”), and execute the “Live” instruction for the designated APP when the configuration conditions are met, so as to achieve the effect of advertising “Live” and earn “Live” fees from it.
This has led to the repeated occurrence of abnormal phenomena such as “antivirus cannot be killed”, “keys failing for no reason”, and “automatic downloading of junk software” in those Gionee phones that have been implanted with viruses.
I thought I was buying a high-secret mobile phone, but I didn’t expect it to become a tool for others to collect money illegally. For the political and business people, especially those in important positions, it is undoubtedly a flies swallowed by mistake.

“Cure all diseases”
We must worry about hacker attacks externally, and internally we must worry about the various “small actions” made by manufacturers behind the scenes. Faced with the problem of mobile phone information security, are we at nothing?
actually not.
First, we should avoid handling classified information on mobile phones, especially information related to national security and commercial secrets, so as to cut off the leakage of classified information.
Secondly, if you need to communicate and process secret-related information, it must be carried out in a standard secret-related conference room. Before participating in the conference, the mobile phone must be placed in a mobile phone shielding cabinet that meets the national security standards.
Finally, when communicating important information, in order to prevent hackers from monitoring the mobile phone through viruses, so as to monitor and monitor, the mobile phone can be placed in the mobile phone signal shielding package, and the signal and network of the mobile phone can be cut off anytime and anywhere.
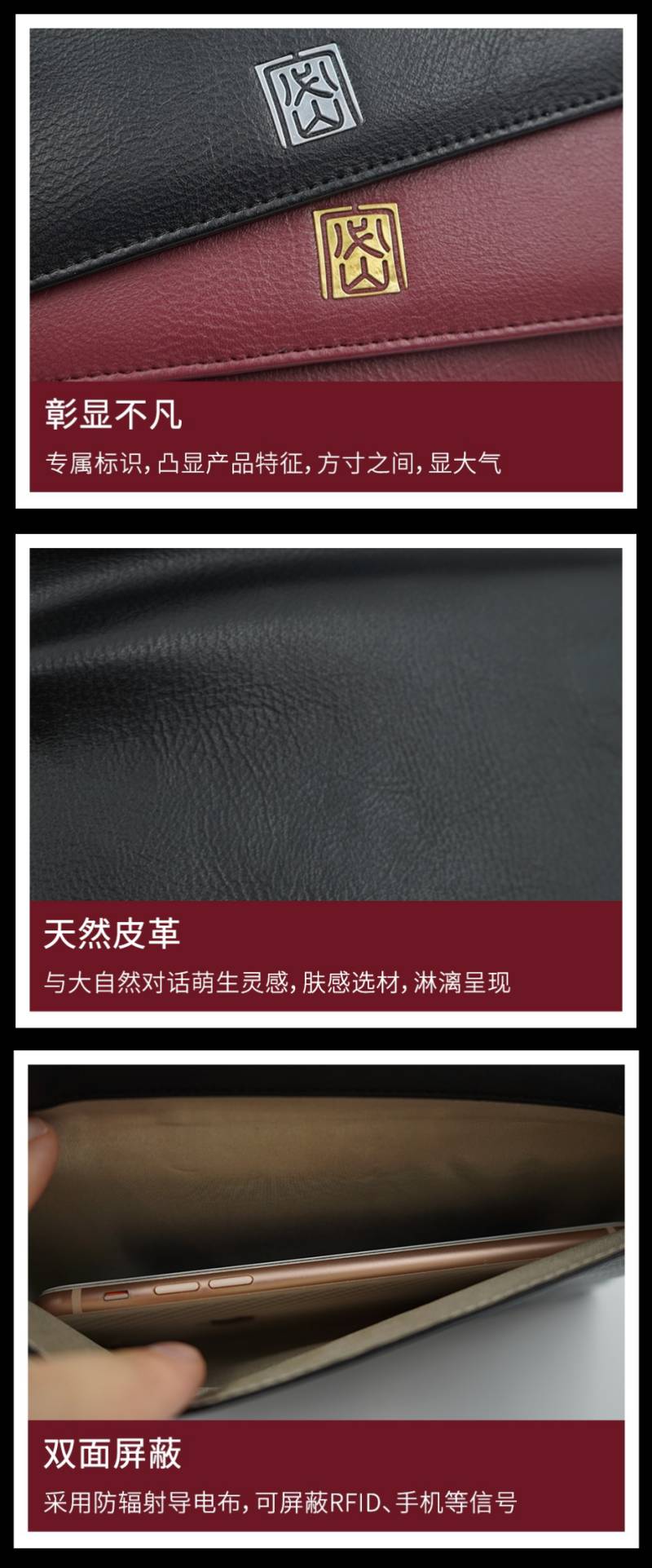
Mobile phone signal shielding package
The so-called mobile phone shielding bag can not only be used as an ordinary storage wallet, but also prevent positioning, anti-eavesdropping, anti-disturbance, anti-radiation, anti-theft brushing, effectively shield signals and prevent information leakage, and is very suitable for use by personnel involved in secrets.
A powerful mobile phone shielding bag, in addition to high-quality materials and exquisite craftsmanship, there will also be a special place for shielding mobile phones in the bag, and you can freely choose whether to shield or not.
The inside of the shielding layer of the body is made of metal copper and metal nickel, which can effectively shield scanning rays and shield signals. When the mobile phone is placed in the shielding layer and the cover is closed, the mobile phone will be in a “sleep state” within 30 seconds, and within 30 seconds after being taken out Normal functions will be restored.
Information security is no small matter, build a secure firewall
“Black hands” are ubiquitous in stealing secrets, and they are often overwhelming. But sometimes, a mobile phone shielding bag that can be carried with you can effectively block the connection between the mobile phone and the outside world, realize the invisibility of the mobile phone, and achieve the purpose of protecting secrets.
Take personal protection, strengthen the awareness of confidentiality, and use mobile phones rationally, so that the thief has nowhere to take advantage.
-END-
Some texts and pictures are from the Internet, and the copyright belongs to the original author.